Duo MFA Changes Coming Soon
Posted Date: February 28, 2024
UPDATE: All Northwestern students, faculty, staff, and affiliates were contacted via email on Thursday, May 16, with an update on this initiative. The project includes turning off the SMS passcode and phone call options in Duo and enabling Duo’s new Verified Push. Northwestern IT is turning off the SMS passcode and phone call options and enabling Verified Push for everyone at Northwestern on Wednesday, July 10.
Northwestern IT’s Multi-factor Authentication (MFA) Enhancement initiative is underway and intended to better secure University systems and protect the identities of the community against evolving cyberattacks designed to get through existing MFA protections. The effort includes turning off the telephony option in Duo (SMS passcode and phone call) and enabling Duo’s new Verified Push option.
Anyone still using telephony options is encouraged to take action now to move to more secure methods of MFA. We are implementing both of these changes on a rolling basis to University community members this spring. Additional communications with specific dates for different members of the University community are forthcoming.
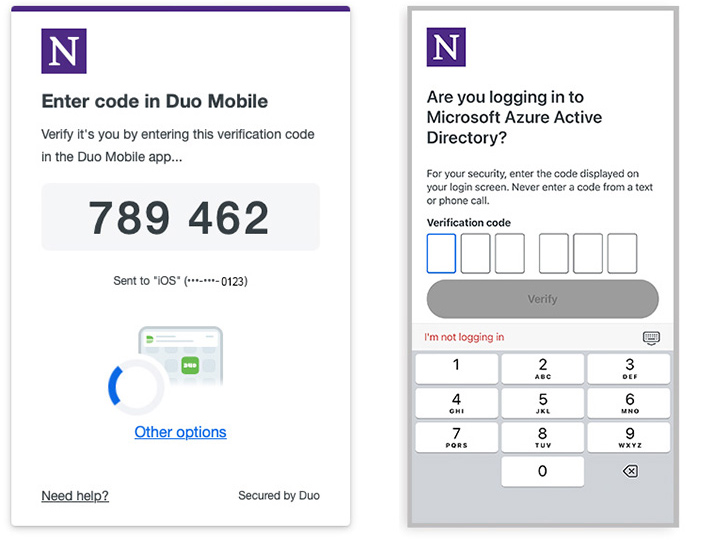
What is Verified Push?
Verified Push introduces a new verification code option for Duo Push. It provides additional security against push harassment and fatigue attacks by asking users to enter a verification code while approving an authentication request. When enabled, users logging into an application that requires MFA will see a numeric code six digits in length in the prompt (see the example to the right). This code must then be entered to approve the Duo Push request on your authentication device. This change in method ensures you cannot accidentally approve login requests.
Accessing Verified Push
For individuals already using the Duo Mobile app and running version 4.16 (or higher) on Android and 4.17 (or higher) on iOS, there is nothing to do now. The authentication experience will remain unchanged until Northwestern IT enables Verified Push this spring. Anyone needing to check their Duo app version can review this Knowledge Base article.
Individuals Currently Using Telephony (SMS and Phone Call) Options
Anyone still using telephony in Duo can continue to do so until the telephony option is turned off later this spring. However, we encourage users to take action now, if possible, to move to more secure methods of MFA. Current telephony users can review the various options below, but they will also receive multiple communications in the coming months to offer information on available options.
Is Duo Push the only option for MFA?
While Duo Verified Push is the recommended solution for MFA, Northwestern IT will continue to support codes generated by the Duo Mobile app, hardware authenticators (YubiKeys), Duo Tokens, and biometric authenticators such as TouchID or Windows Hello.
Thank you for helping to secure Northwestern’s University systems and protect the data within them. If you have any questions, please direct them to the IT staff in your specific schools and units or to the Northwestern IT Information Security Office.