Don't Take the Bait
Recognizing Phishing Attempts
 Email scams and phishing messages are types of electronic fraud that request recipients to disclose information or perform other potentially harmful actions. These types of emails appear to come from reliable sources like Northwestern, your banking institution, and more. They often contain urgent requests that require the recipient to provide sensitive information―passwords, account numbers, etc.―by either replying to the email directly or by entering information on a bogus website.
Email scams and phishing messages are types of electronic fraud that request recipients to disclose information or perform other potentially harmful actions. These types of emails appear to come from reliable sources like Northwestern, your banking institution, and more. They often contain urgent requests that require the recipient to provide sensitive information―passwords, account numbers, etc.―by either replying to the email directly or by entering information on a bogus website.
To prevent email scams from reaching the University’s central email server, Northwestern’s Email Defense System (EDS), powered by Proofpoint, blocks the majority of malicious messages from being distributed to the University community. However, malicious and junk emails occasionally slip through this security net. If you believe a phishing scam has reached your inbox, please report the email to the Information Security Office. View recent phishing attempts reported at Northwestern.
Choppy Waters Ahead
Navigating Your Inbox
Phishers may have gotten smarter, but we have too! Knowing what to look out for can significantly reduce your risk of being phished. Tab through the following examples to learn about the common warning signs.
Work From Home
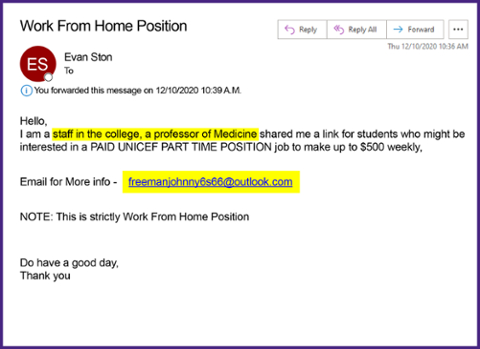
This attempt tries to prompt a response to a non-Northwestern email address. Remember that sending messages to unknown users or clicking on unknown links can leave your information vulnerable to scammers. It is important to recognize this kind of phish, so you know to avoid clicking on any links or sending any messages.
How to Spot the Phish
- False sender/false credibility - Scammers try to fool you into thinking the email is legitimate. Does the email address match the sender's identity? Are the sender's credentials specific and clear?
- Bad grammar and typos - Poorly written sentences, bad grammar, and misspelled words indicate that the email is probably a phishing scam.
Urgent Request
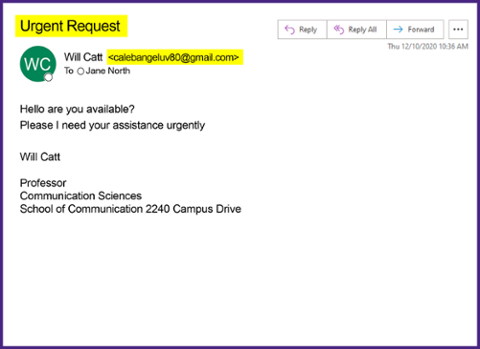
This phishing scam is posing as faculty to prompt a response, but the message was sent from a non-Northwestern email address. Remember that sending messages to unknown users can leave your information vulnerable to scammers. It is important to recognize this kind of phish, so you know to avoid replying to their message.
How to Spot the Phish
- Sense of urgency - Urgent requests require the recipient to provide sensitive information—passwords, account numbers, etc.—by either replying to the email directly or entering information on a fraudulent website.
- Forged email address - The sender's email address may be forged, even if it looks legitimate. This address is suspect because the sender does not match the name used in the body of the message.
Action Required
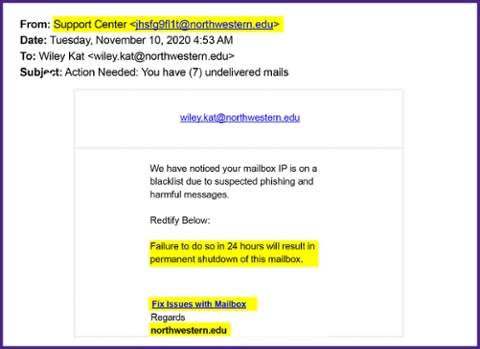
Scammers claim there is a problem with your account and then tell you the way to fix it is to click a link and enter your credentials. Odds are, this is a disguised link that leads to a fraudulent website that will record your information. Remember that clicking on unknown links can leave your information vulnerable to scammers. If someone has your login information, they can access your Northwestern account. It is important to recognize this kind of phish, so you know to avoid the link and don’t give your credentials. Northwestern will never ask for personally identifiable information.
How to Spot the Phish
- False sender/false credibility - Scammers try to fool you into thinking the email is legitimate. Does the email address match the sender's identity? Are the sender's credentials specific and clear?
- Sense of urgency - Urgent requests require the recipient to provide sensitive information—passwords, account numbers, etc.—by either replying to the email directly or by entering information on a fraudulent website.
- Request for personal information - Be wary of any message that asks for your personal information, as it is likely a phishing attempt.
- Disguised or modified link - Never click a link that requests personal information. When you hover your mouse over a link, the actual URL you are being directed to is displayed in a pop-up or at the bottom of your browser window so you can understand where the link is pointing.
Voicemail
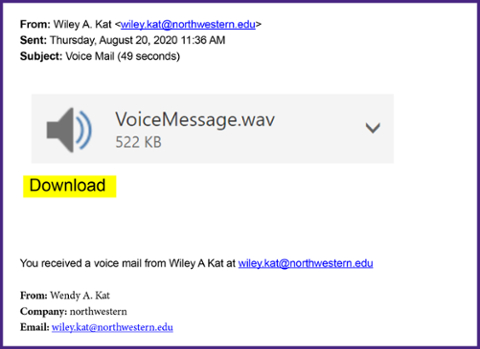
This phishing scam is asking you to download an attachment (in this case, it is a voicemail, but it is similar to clicking a disguised link with a call to action). However, downloading an unknown file can allow a virus to infiltrate your computer and leave your information vulnerable to scammers. It is important to recognize this kind of phish, so you know to avoid downloading suspicious attachments.
How to Spot the Phish
- Unprofessional email title - Legitimate organizations typically do not use unprofessional formatting in the messages they send to clients.
- Disguised or modified link - When you hover your mouse over a link, the actual URL you are being directed to is displayed in a pop-up or at the bottom of your browser window so you can understand where the link is pointing. If the link in the email and the URL displayed are not identical, there is a possibility that you are being directed to a fraudulent site.
- Official looking signatures - The sender's email address may be forged, even if it looks legitimate.
Waiting for Payment
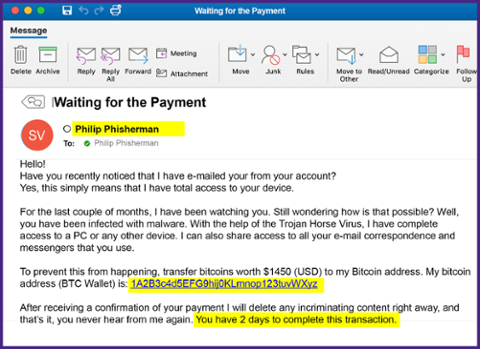
This email appears to be sent from your own account and scares you by claiming they have power over your device or information. The scammer then threatens or blackmails you. Remember that clicking on unknown links can leave your information vulnerable to scammers. It is important to recognize this kind of phish, so you know to avoid the link and extortion attempt.
How to Spot the Phish
- Forged email address - The sender's email is spoofing the recipient's email to make it appear legitimate.
- Sense of urgency - Phishing emails typically warn of a sudden change to an account and ask you to act immediately to verify your account.
- Bad grammar and typos - Poorly written sentences, bad grammar, and misspelled words indicate that the email is probably a phishing scam.
Many Phish in the Sea
Other Types of Phishing
Phishing isn’t just for email anymore. Be aware of attacks through phone calls, texts, or other online messaging applications. Make sure you are on the lookout for these variants below on the traditional, mass emailed phishing attack.

SMISHING
These scams attempt to trick users into supplying content or clicking on links in SMS messages on their mobile devices. Flaws in how caller ID and phone number verification systems work make this an increasingly popular attack that is difficult to stop.
SPEAR PHISHING
This kind of attack uses well-crafted, targeted messages, often aimed at or made to appear as coming from a trusted VIP source. The attack is usually framed as urgent or time-sensitive and aims to gain credentials or authorization to conduct financial transactions on behalf of an organization. This attack is also sometimes called "whaling."

VISHING
These are calls from attackers claiming to be government agencies such as the IRS, software vendors like Microsoft, or services offering to help with benefits or credit card rates. Attackers will often appear to be calling from a local number close to yours.
Use Your Tackle Box
Best Practices to Avoid Getting Hooked
The best defense against malicious email attempts is an educated user. Remember to always be cautious about opening any attachments or downloading any files from emails you receive, regardless of who sent them. When you receive any email requesting personally identifiable information, follow these best practices to protect yourself and the University.
Never reply to an unsolicited email
Messages that ask for your personal information, including requests for NetID passwords, Social Security Numbers, or requests for credit card information, should not be trusted. Most institutions (Northwestern, your bank or credit card company, etc.) will not email you requesting this type of information.
Do not click on links directly from emails
Open a new browser and find the supposed institution’s website yourself through a search engine or URL bar. You can also bookmark the NUValidate pages to update or verify your NetID password.
Be alert for suspicious emails
Messages with suspicious, misspelled, or awkward language, or those that reference non-existent Northwestern departments like "University Webmail Support" or the "Webmail Messaging Center," are examples of scam emails. Pay attention to unusual greetings or signatures from messages purporting to be from your contacts. Compare the message to the list of recent phishing email attempts collected and posted by Northwestern IT.
Delete messages that are confirmed to be phishing
If you confirm or recognize a message to be a phishing attempt, delete it from your "Inbox" and your "Deleted Items" folder to avoid accidentally accessing the web sites within the fraudulent email.
Do not send your personal information
Never send personally identifiable information, such as passwords, credit card account numbers, and Social Security Numbers, through email.
Update software often
Regularly update and use antivirus and antispyware software and your firewall. Be sure your applications and antivirus software are the most current version.
Think You Spotted a Scam?
Report It!
 If you are unsure about the legitimacy of an email claiming to be from Northwestern, compare it to the recent list of attempts at Northwestern. If it is not listed, immediately forward the complete message with email message headers to security@northwestern.edu. Remember, Northwestern will never ask for personally identifiable information.
If you are unsure about the legitimacy of an email claiming to be from Northwestern, compare it to the recent list of attempts at Northwestern. If it is not listed, immediately forward the complete message with email message headers to security@northwestern.edu. Remember, Northwestern will never ask for personally identifiable information.
If you believe you have responded to a malicious email, change your NetID password immediately, email security@northwestern.edu, and call the Northwestern IT Service Desk at 847-491-4357 (1-HELP) to report the scam.

 Email scams and phishing messages are types of electronic fraud that request recipients to disclose information or perform other potentially harmful actions. These types of emails appear to come from reliable sources like Northwestern, your banking institution, and more. They often contain urgent requests that require the recipient to provide sensitive information―passwords, account numbers, etc.―by either replying to the email directly or by entering information on a bogus website.
Email scams and phishing messages are types of electronic fraud that request recipients to disclose information or perform other potentially harmful actions. These types of emails appear to come from reliable sources like Northwestern, your banking institution, and more. They often contain urgent requests that require the recipient to provide sensitive information―passwords, account numbers, etc.―by either replying to the email directly or by entering information on a bogus website.






 If you are unsure about the legitimacy of an email claiming to be from Northwestern, compare it to the recent list of
If you are unsure about the legitimacy of an email claiming to be from Northwestern, compare it to the recent list of